git / gnutls / handshake failed / nginx ciphers
When trying to keep up with all the TLS/SSL security changes, you need
to modify your nginx config every now and then.
The good TLS config may look like this:
# nginx.conf: http {
ssl_certificate /etc/ssl/MY_DOMAIN.pem;
ssl_certificate_key /etc/ssl/MY_DOMAIN.key;
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
ssl_ciphers ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES256-SHA;
ssl_session_cache shared:SSL:5m;
ssl_session_timeout 5m;
ssl_prefer_server_ciphers on;
add_header Strict-Transport-Security "max-age=15768000; includeSubDomains";
And the above config is accompanied by a fairly good A grade from the Qualys SSL Labs Analyzer.
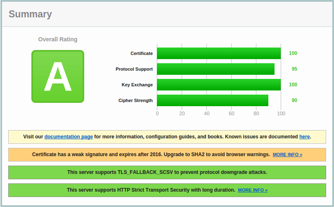
But, it turns out that a too strict config will cause failures with even recent versions of GnuTLS.
See this example:
$ git clone https://MY_GIT_SERVER/abc
Cloning into 'abc'...
fatal: unable to access 'https://MY_GIT_SERVER/abc/': gnutls_handshake() failed: Handshake failed
Okay, that was too strict apparently. Which versions?
$ lsb_release -a 2>/dev/null | grep ^Description
Description: Ubuntu 14.04.1 LTS
$ dpkg -l git libgnutls26 | grep ^ii | awk '{print $2 " " $3}'
git 1:1.9.1-1
libgnutls26:amd64 2.12.23-12ubuntu2.1
At first, it looked like gnutls-cli-debug would provide the useful
info.
$ gnutls-cli-debug MY_GIT_SERVER
Resolving 'MY_GIT_SERVER'...
Connecting to '1.2.3.4:443'...
Checking for SSL 3.0 support... no
Checking whether %COMPAT is required... yes
Checking for TLS 1.0 support... no
...
Server does not support any of SSL 3.0, TLS 1.0 and TLS 1.1
However, fixing that required the addition of RC4-SHA to the
ssl_ciphers list; a cipher that’s not real strong.
$ gnutls-cli-debug MY_GIT_SERVER
Resolving 'MY_GIT_SERVER'...
Connecting to '1.2.3.4:443'...
Checking for SSL 3.0 support... no
Checking whether %COMPAT is required... yes
Checking for TLS 1.0 support... yes
Checking for TLS 1.1 support... yes
...
Good, GnuTLS is happy.
But, that got us a grade B. And, worst of all, it didn’t fix the git
connection handshake error.
Luckily, git was satisfied when we added DHE-RSA-AES256-SHA instead.
And it did not mess up the rating too much.
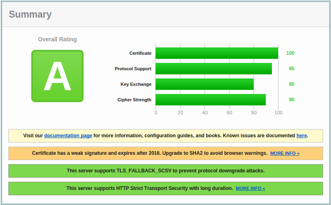
Thus, the working config:
ssl_ciphers ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-RSA-AES256-SHA:DHE-RSA-AES256-SHA;

